Analysis of WezRat Malware; Check point Findings
Check Point Research finds WezRat Malware
New CheckPoint research discovered a new remote access trojan and information stealer used by Iranian state-sponsored actors to conduct reconnaissance of compromised endpoints and execute malicious commands.
The Malware is known as WezRat, and was sent to multiple Israeli organizations in a wave of emails impersonating the Israeli National Cyber Directorate (INCD). Check Point Research tracks this malware family as WezRat and distributed in a large-scale phishing campaign.
What does WezRat do?
WezRat is assessed to be the work of Cotton Sandstorm, an Iranian hacking group now known as Emennet Pasargad and, more recently, Aria Sepehr Ayandehsazan (ASA).
The malware can execute commands, take screenshots, upload files, perform keylogging, and steal clipboard content and cookie files. Some functions are performed by separate modules retrieved from the command and control (C&C) server in the form of DLL files,creating less suspicion.
The malware was first documented late last month by U.S. and Israeli cybersecurity agencies, describing it as an “exploitation tool for gathering information about an end point and running remote commands.”
WezRat is written in C++ and researchers observed two samples of the backdoor recently used. The primary difference between them is using OLLVM common obfuscation techniques such as opaque predicates and control flow flattening. The obfuscated variant also supports fewer commands.
Checkpoint provide an analysis of the latest non-obfuscated version with full command support (md5: 6b0d7b2e422a93e81ceed3645d36dd40, internally called bd.exe).
WezRat has been active for over a year and gained additional modules, and its backend infrastructure has undergone various changes.
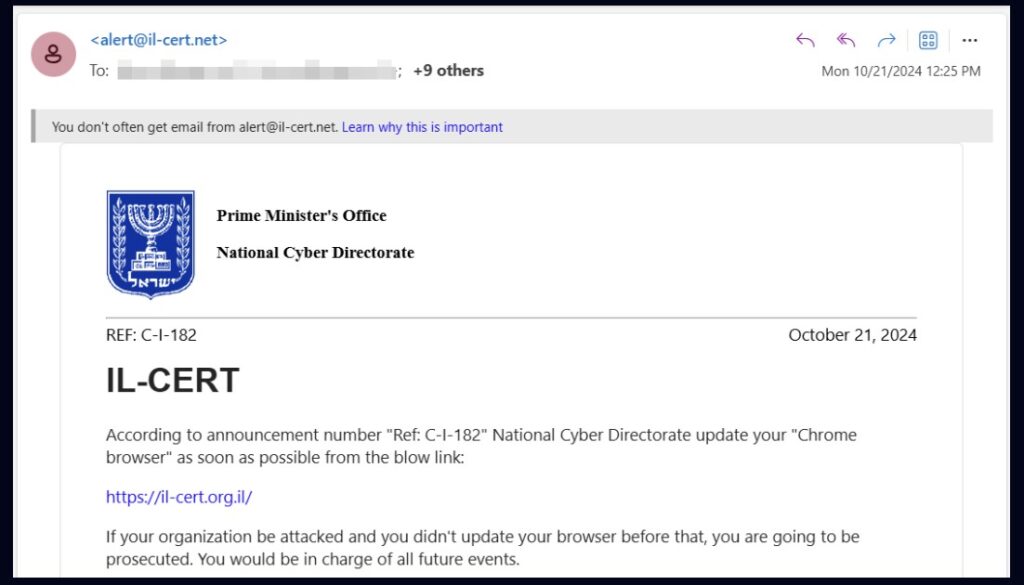
On October 21, 2024, multiple emails impersonating the Israeli National Cyber Directorate (INCD) were sent to various Israeli organizations. These emails were sent from the fraudulent address alert@il-cert[.]net and warned recipients of an urgent necessity to update their Chrome browser.
Joint advisory released
US Department of Treasury, and the Israeli National Cybersecurity Directorate (INCD) released a joint Cybersecurity Advisory regarding recent activities of the Iranian cyber group Emennet Pasargad.
The advisory details operations that have impacted various countries, including the US, France, Israel, and Sweden.
Cybersecurity analysts at Check Point observed that the cybersecurity advisory highlights the Emennet Pasargad’s recent operations:-
Mid-2023: Hacked a Swedish SMS service to distribute messages related to Quran burnings
December 2023: Compromised a US-based IPTV streaming company to broadcast messages about the Israel-HAMAS conflict
Mid-2024: Launched a cyber-enabled disinformation campaign during the Summer Olympics, targeting Israeli athletes
Fake Google Chrome Update campaign
When emails were sent from the fraudulent address alert@il-cert[.]net and warned recipients of an urgent necessity to update their Chrome browser, the emails included a link that approved to direct users to the legitimate INCD site. il-cert.org.il, but in fact, led to a lookalike domain, il-cert[.]net. From there, victims would automatically download a file named Google Chrome Installer.msi and then be redirected to the legitimate INCD website.
(Figure: Courtesy: research.checkpoint)
