Critical SAP NetWeaver Zero-day Vulnerability Exploited in the Wild
As per researchers hackers are actively exploiting a critical unrestricted-file-upload vulnerability in SAP NetWeaver Visual Composer. Regarding this urgent patch has been released by SAP to fix CVE-2025-31324, a zero-day vulnerability in SAP NetWeaver Visual Composer.
Critical SAP NetWeaver Zero-day Vulnerability Exploited in the Wild
The vulnerability in SAP NetWeaver Visual Composer that may have allowed unauthenticated and unauthorized code execution in certain Java Servlets.
Several cybersecurity companies have reported active exploitation in the wild.
Summary
| OEM | SAP |
| Severity | Critical |
| CVSS Score | 10.0 |
| CVEs | CVE-2025-31324 |
| POC Available | No |
| Actively Exploited | Yes |
| Exploited in Wild | Yes |
| Advisory Version | 1.0 |
Overview
This vulnerability enables remote uploading and execution of malicious files by unauthenticated attackers, potentially compromising the entire system.
It is highly advised to implement patching or mitigation measures right away in order to guard against possible espionage, sabotage, data theft, and operational disruption.
| Vulnerability Name | CVE ID | Product Affected | Severity | CVSS Score |
| Missing Authorization in Metadata Uploader | CVE-2025-31324 | SAP | Critical | 10.0 |
Technical Summary
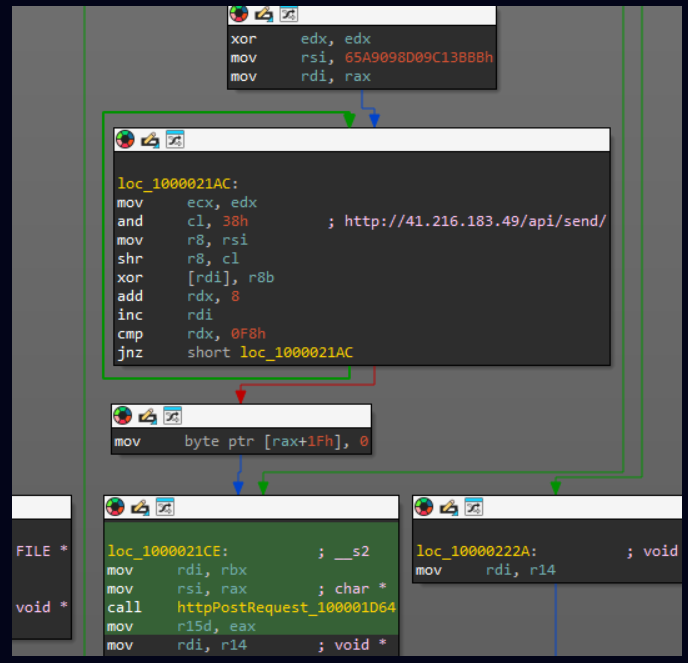
The vulnerability stems from a missing authorization check in the Metadata Uploader component of SAP NetWeaver Visual Composer.
Attackers can exploit this by sending crafted unauthenticated POST requests to the development server/meta data uploader endpoint, allowing them to upload arbitrary JSP webshell files.
Once uploaded, attackers can interact with these shells via simple GET requests to execute arbitrary commands, resulting in remote code execution (RCE) with <sid>adm operating system privileges — effectively giving full control over SAP systems.
| CVE ID | System Affected | Vulnerability Details | Impact |
| CVE-2025-31324 | SAP NetWeaver Visual Composer (VCFRAMEWORK 7.50) | Missing authorization check at /developmentserver/metadatauploader enables unauthenticated malicious file uploads. Webshells planted can be used to execute OS-level commands, deploy additional malware, and move laterally across the network. | Full system compromise including: – Remote Command Execution – Privilege Escalation – Data Exfiltration – Ransomware Deployment – Potential Espionage/Sabotage/Fraud |
Key Exploitation Details:
- Exploited Path: /developmentserver/metadatauploader
- Common Webshell Files: helper.jsp, cache.jsp, and others with randomized names.
- Post-Exploitation Tools:
- Brute Ratel: Used for C2 operations, credential theft, privilege escalation.
- Heaven’s Gate: 32-to-64 bit transition technique for evading endpoint detection.
Risk Factors:
- Systems where Visual Composer is enabled (even though it is not enabled by default).
- Systems exposed to the internet.
- Systems without custom security measures protecting the Metadata Uploader endpoint.
Remediation:
- Apply SAP Patch: Updated the patches released by SAP without waiting for routine patch cycles.
- Restrict Access: Block external access to the /development server/metadata uploader endpoint via firewall or reverse proxy rules.
- Disable Visual Composer: If Visual Composer is not critical to business operations, disable it to remove the attack surface.
Recommendations:
- Conduct Threat Hunting:
Scan for suspicious JSP files (e.g., helper.jsp, cache.jsp) in these directories:
- /j2ee/cluster/apps/sap.com/irj/servlet_jsp/irj/root
- /j2ee/cluster/apps/sap.com/irj/servlet_jsp/irj/work
- /j2ee/cluster/apps/sap.com/irj/servlet_jsp/irj/work/sync
- Monitoring and SIEM: Forward logs from the NetWeaver server to SIEM tools and monitor for unauthorized file upload activity.
- Utilize Open-Source Tools: Use scanners (such as those released by Onapsis) to check system vulnerability.
Conclusion:
Given the criticality and active exploitation of CVE-2025-31324, organizations running SAP NetWeaver Visual Composer should prioritize patching and mitigation efforts. The potential for full system compromise, ransomware attacks, and data exfiltration represents a severe business risk. Immediate action is strongly advised to secure SAP environments and prevent exploitation.
References: