Advisory on MUT-8694: Threat Actors Exploiting Developer Trust in Open-Source Libraries
MUT-8694: Threat Actors Exploiting Developer Trust in Open-Source Libraries
Overview
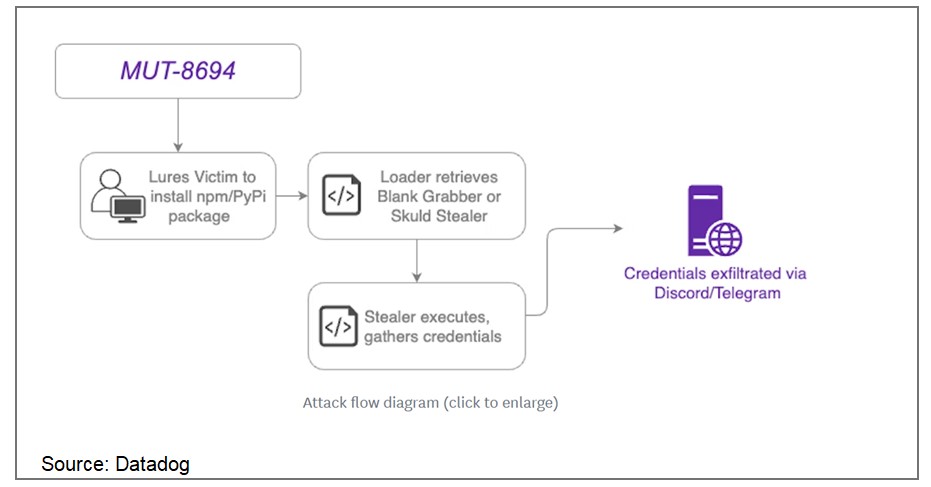
In November 2024, a supply chain attack designated as MUT-8694 was identified, targeting developers relying on npm and PyPI package repositories. This campaign exploits trust in open-source ecosystems, utilizing typosquatting to distribute malicious packages. The malware predominantly affects Windows users, delivering advanced infostealer payloads.
MUT-8694 Campaign Details
The threat actors behind MUT-8694 use malicious packages that mimic legitimate libraries to infiltrate developer environments. The campaign employs techniques such as:
- Typosquatting: Using package names that closely resemble popular or legitimate libraries.
- Payload Delivery: Embedded scripts download malware such as Blank Grabber and Skuld Stealer hosted on GitHub and repl.it.
- Targeted Ecosystems: npm and PyPI, critical platforms for developers.
Source: Datadog
Key Findings
One identified package, larpexodus (version 0.1), executed a PowerShell command to download and run a Windows PE32 binary from github[.]com/holdthaw/main/CBLines.exe. Analysis revealed the binary was an infostealer malware, Blank Grabber, compiled from an open-source project hosted on GitHub. Further inspection of the repository exposed another stealer, Skuld Stealer, indicating the involvement of multiple commodity malware samples.
Capabilities of Malware
The deployed malware variants include advanced features that allow:
- Credential Harvesting: Exfiltrating usernames, passwords, and sensitive data.
- Cryptocurrency Wallet Theft: Targeting and compromising crypto assets.
- Application Data Exfiltration: Stealing configuration files from popular applications
Affected Packages
Some known malicious packages include:
- larpexodus (PyPI): Executes a PowerShell script to download malware.
- Impersonations of npm libraries: Host binaries leading to infostealer deployment.
Remediation:
To mitigate the risks associated with this attack, users should:
- Audit Installed Packages: Use tools like npm audit or pip audit to identify vulnerabilities.
- Validate Package Sources: Verify package publishers and cross-check names carefully before installation.
- Monitor Network Activity: Look for unusual connections to GitHub or repl.it domains.
- Use Security Tools: Implement solutions that detect malicious dependencies.
General Recommendations:
- Avoid downloading software from unofficial or unverified sources.
- Regularly update packages and dependencies to the latest versions.
- Conduct periodic security awareness training for developers and IT teams.
References:

