Banshee Stealer: A Growing Threat to macOS Users
Overview
Cybersecurity researchers at Check Point Research (CPR) have discovered a sophisticated macOS malware called Banshee Stealer, putting over 100 million macOS users globally at risk. The malware, designed to exfiltrate sensitive user data, demonstrates advanced evasion techniques, posing a significant threat to users and organizations relying on macOS.
Key Threat Details:
Malware Capabilities:
- Data Theft: Banshee Stealer targets browser credentials, cryptocurrency wallets, and sensitive files, compromising user security.
- User Deception: It displays fake system pop-ups to trick users into revealing their macOS passwords, facilitating unauthorized access.
- Encryption and Exfiltration: Stolen data is compressed, encrypted, and transmitted to command-and-control (C&C) servers through stealthy channels, making detection challenging.
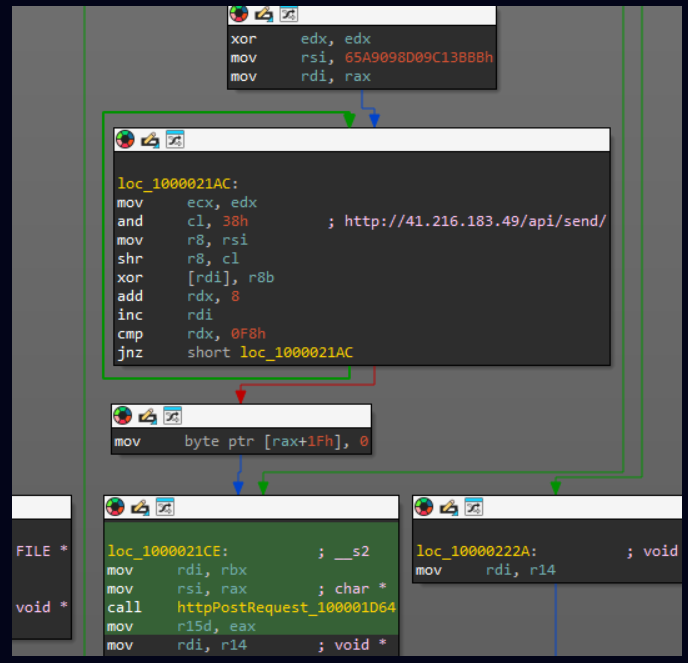
C&C decryption Source: Cybersecurity News
Evasion Tactics:
- Advanced Encryption: The malware utilizes encryption techniques similar to Apple’s XProtect, camouflaging itself to evade detection by traditional antivirus systems.
- Stealth Operations: It operates seamlessly within system processes, avoiding scrutiny from debugging tools and remaining undetected for extended periods.
Distribution Mechanisms:
- Phishing Websites: Banshee Stealer impersonates trusted software downloads, including Telegram and Chrome, to deceive users into downloading malicious files.
- Fake GitHub Repositories: It distributes DMG files with deceptive reviews and stars to gain user trust, facilitating the spread of the malware.
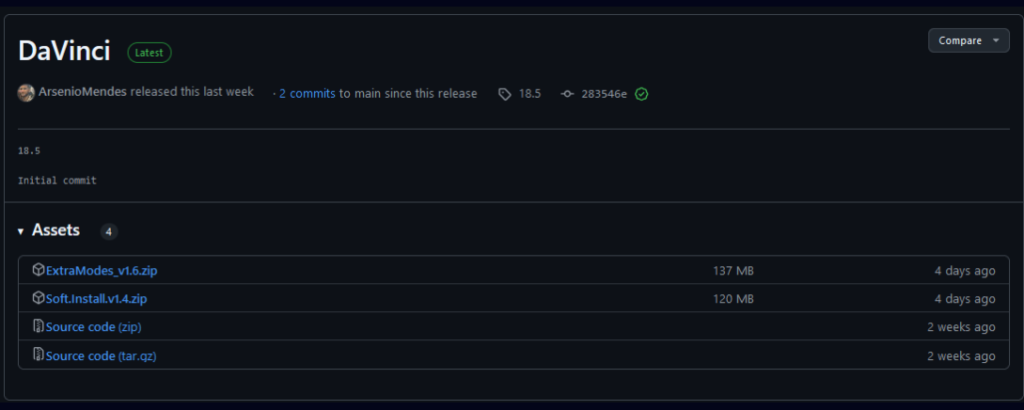
Repository releases source: Cybersecurity News
Recent Developments:
- Expanded Targeting: The latest version of Banshee Stealer has removed geographic restrictions, such as the Russian language check, broadening its target audience globally.
- Source Code Leak: Following a source code leak, there has been increased activity, enabling other threat actors to develop variants and intensify the threat landscape.
Impact:
- Users: Compromised browser data, cryptocurrency wallets, and personal files can lead to identity theft and financial losses.
- Organizations: Potential data breaches can result in reputational damage, financial losses, and legal implications.
- Global Threat: The malware’s expanded targeting underscores the need for enhanced vigilance among macOS users worldwide.
Indicators of Compromise (IOCs):
The IOCs listed below are associated with the threat. For the full list of IOCs, please refer to the link .
| IP Address and Domain | File Hash |
| 41.216.183[.]49 | 00c68fb8bcb44581f15cb4f888b4dec8cd6d528cacb287dc1bdeeb34299b8c93 |
| Alden[.]io | 1dcf3b607d2c9e181643dd6bf1fd85e39d3dc4f95b6992e5a435d0d900333416 |
| api7[.]cfd | 3bcd41e8da4cf68bb38d9ef97789ec069d393306a5d1ea5846f0c4dc0d5beaab |
| Authorisev[.]site | b978c70331fc81804dea11bf0b334aa324d94a2540a285ba266dd5bbfbcbc114 |
Recommendations:
To mitigate the risks associated with Banshee Stealer, consider implementing the following proactive measures:
- Avoid Untrusted Downloads:
- Refrain from downloading software from unverified sources, particularly free or “cracked” versions.
- Verify the authenticity of GitHub repositories before downloading any files.
- Strengthening System Defenses:
- Regularly update macOS and all installed applications to patch known vulnerabilities.
- Deploy advanced security solutions with real-time threat detection and proactive intelligence.
- Enhance Awareness and Training:
- Educate users on identifying phishing websites and suspicious downloads.
- Encourage caution when responding to system prompts or entering credentials.
- Enable Two-Factor Authentication (2FA):
- Secure accounts with 2FA to minimize the impact of stolen credentials.
- Monitor System Activity:
- Regularly review system logs for unauthorized changes or suspicious activity.
- Use tools to monitor unexpected outgoing data transmissions.
- Utilize threat intelligence feeds to detect and block IOCs like malicious IPs, domains, and file hashes.
- Continuously monitor network traffic, emails, and file uploads to identify and mitigate threats early.
Conclusion:
The rise of the Banshee malware exemplifies the increasing sophistication of threats targeting macOS. Users and organizations must adopt layered security defenses, maintain vigilance, and prioritize awareness to mitigate the risks of advanced malware like Banshee. By leveraging updated tools and practices, you can safeguard critical systems and data from evolving cyber threats.
References:

