Blue Yonder SaaS giant breached by Termite Ransomware Gang
The company acknowledged it is investigating claims by a public threat group linked to the November ransomware attack.
Continue ReadingThe company acknowledged it is investigating claims by a public threat group linked to the November ransomware attack.
Continue ReadingMUT-8694: Threat Actors Exploiting Developer Trust in Open-Source Libraries
Overview
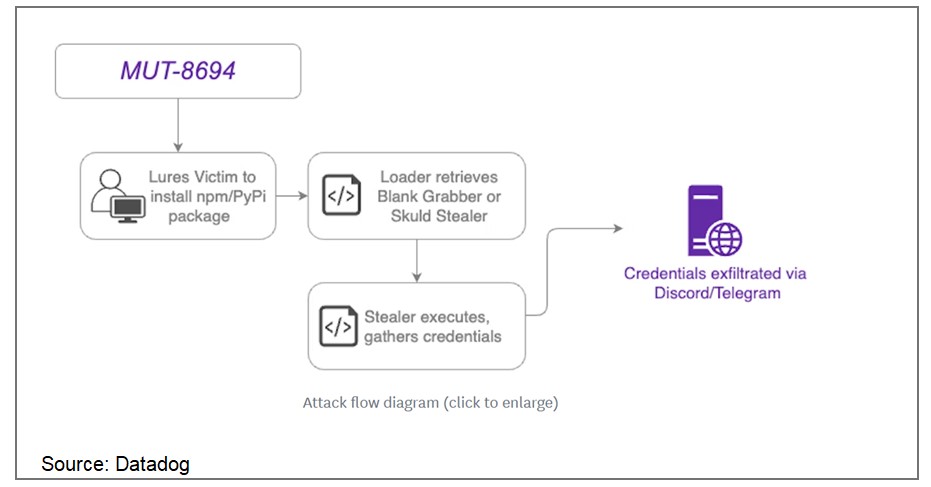
In November 2024, a supply chain attack designated as MUT-8694 was identified, targeting developers relying on npm and PyPI package repositories. This campaign exploits trust in open-source ecosystems, utilizing typosquatting to distribute malicious packages. The malware predominantly affects Windows users, delivering advanced infostealer payloads.
MUT-8694 Campaign Details
The threat actors behind MUT-8694 use malicious packages that mimic legitimate libraries to infiltrate developer environments. The campaign employs techniques such as:
Source: Datadog
Key Findings
One identified package, larpexodus (version 0.1), executed a PowerShell command to download and run a Windows PE32 binary from github[.]com/holdthaw/main/CBLines.exe. Analysis revealed the binary was an infostealer malware, Blank Grabber, compiled from an open-source project hosted on GitHub. Further inspection of the repository exposed another stealer, Skuld Stealer, indicating the involvement of multiple commodity malware samples.
Capabilities of Malware
The deployed malware variants include advanced features that allow:
Affected Packages
Some known malicious packages include:
Remediation:
To mitigate the risks associated with this attack, users should:
General Recommendations:
References:
OEM | Veeam |
Severity | Critical |
Date of Announcement | 2024-12-05 |
CVSS Score | 9.9 |
CVE | CVE-2024-42448, CVE-2024-42449 |
Exploited in Wild | No |
Patch/Remediation Available | Yes |
Advisory Version | 1.0 |
Two critical vulnerabilities in the Veeam Service Provider Console (VSPC) enable attackers to perform unauthenticated remote code execution (RCE) and arbitrary file deletion. These flaws present severe threats to the infrastructure of managed service providers that depend on VSPC for their operations.
Vulnerability Name | CVE ID | Product Affected | Severity | CVSS Score |
Veeam Service Provider Console RCE | CVE-2024-42448 | Veeam Service Provider Console | Critical | 9.9 |
NTLM Hash Leak and Arbitrary File Deletion on Server | CVE-2024-42449 | Veeam Service Provider Console | High | 7.1 |
CVE ID | System Affected | Vulnerability Details | Impact |
CVE-2024-42448 | VSPC v8.1.0.21377 and all earlier versions. | This critical remote code execution (RCE) vulnerability allows unauthenticated attackers to execute arbitrary code on the Veeam Service Provider Console server. It exploits a flaw in the server's handling of input, enabling attackers to compromise the entire system. | Allows attackers to execute arbitrary code on the server remotely. |
CVE-2024-42449 | VSPC v8.1.0.21377 and all earlier versions. | This vulnerability allows attackers, via an authorized VSPC management agent, to leak the NTLM hash of the VSPC server service account and delete arbitrary files on the server. Exploitation requires valid credentials for an agent authorized by the VSPC server. | Permits authorized management agents to delete arbitrary files from the VSPC server. |
Godot is a platform that host open source game development, where new Malware loader installed in its programming language
At least 17,000 devices were infected with infostealers and cryptojackers so far.
As per researchers cyber criminals have been building malicious code written in GDScript (Godot’s Python-like scripting language) calling on some 200 GitHub repositories and more than 220 Stargazer Ghost accounts.
Earlier hackers targeted the open sources gaming platform targeting users of the Godot Gaming Engine and researcher’s spotted that GodLoader would drop different malware to the infected devices mostly in RedLine stealer, and XMRig, a popular cryptojacker.
GodLoader, the researchers further explained, was downloaded at least 17,000 times, which is a rough estimate on the number of infected devices. However, the attack surface is much, much larger.
Check Point argues that in theory, crooks could hide malware in cheats, cracks, or modes, for different Godot-built games. Check Point detected four separate attack waves against developers and gamers between September 12 and October 3, enticing them to download infected tools and games.
Looking at the number of popular games developed with Godot, that would put the attack surface at approximately 1.2 million people.
Hackers delivered the GodLoader malware through the Stargazers Ghost Network, a malware Distribution-as-a-Service (DaaS) that masks its activities using seemingly legitimate GitHub repositories.
Technical Details
Godot does not register a file handler for “.pck” files. This means that a malicious actor always has to ship the Godot runtime together with a .pck file. The user will always have to unpack the runtime together with the .pck to the same location and then execute the runtime.
There is no way for a malicious actor to create a “one click exploit”, barring other OS-level vulnerabilities. If such an OS-level vulnerability were used then Godot would not be a particularly attractive option due to the size of the runtime.
Researchers have uncovered the first UEFI bootkit designed specifically for Linux systems, named Bootkitty.
Continue ReadingTailored Security Solutions from Maritime Operations by Intrucept
Continue ReadingNVIDIA has issued a security advisory addressing a critical vulnerability (CVE-2024-0138) discovered in its Base Command Manager software. This flaw, located within the CMDaemon component, poses significant risks, including the potential for remote code execution, denial of service, privilege escalation, information disclosure, and data tampering.
The source of the vulnerability was from insecure temporary file handling, which could lead to a denial of service (DoS) condition on affected systems.
NVIDIA has released patches to address the issue and prevent potential exploitation. This critical flaw can be exploited remotely without any prerequisites, such as user interaction or special privileges, making it highly dangerous.
| Vulnerability Name | CVE ID | Product Affected | Impact | Fixed Version |
| Insecure Temporary File Vulnerability | CVE-2024-0139 | NVIDIA Base Command Manager, Bright Cluster Manager | Medium | Base Command Manager: 10.24.09a; Bright Cluster Manager: 9.0-22, 9.1-19, 9.2-17 |
Technical Summary
NVIDIA confirmed earlier versions, including 10.24.07 and earlier, are not impacted by this vulnerability.
To mitigate the issue, NVIDIA recommends updating the CMDaemon component on all head nodes and software images.
Remediation:
1. Base Command Manager
2. Bright Cluster Manager
3. CMdaemon Update
4. Node Update .
After applying the update, systems should be rebooted or resynchronized with the updated software image to ensure the fix is fully implemented. These measures are essential to eliminate the root cause that created vulnerability and protect systems from potential exploitation.
References:
| CVE ID | System Affected | Platform | Vulnerability Details | Impact |
| CVE-2024-0139 | NVIDIA Base Command Manager (Versions 3, 10) NVIDIA Bright Cluster Manager (Versions 9.0-9.2) | Linux | The vulnerability stems from insecure handling of temporary files in both Base Command Manager and Bright Cluster Manager. Exploiting this flaw could disrupt system availability, potentially causing a denial of service. | Potential denial of service on affected systems. |
Microsoft users had a tough time to send or load attachments to emails when using Outlook, were unable to connect to the server, and in some cases could not log into their accounts.
Microsoft Exchange Online is a platform for business communication that has a mail server and cloud apps for email, contacts, and calendars.
Microsoft mitigated the issue after identification were able to determine the cause of the outages and is rolling out a fix for the issue. That rollout is gradual, however, as outage reports continue to come in at DownDetector.
Impact
The outage left many users unable to communicate with colleagues, particularly as it coincided with the start of the workday in Europe. Frustration quickly spread across social media, with users reporting issues accessing emails and participating in Teams calls
Re-release of November 2024 Exchange Server Security Updates
Summary
| OEM | Microsoft |
| Severity | High |
| Date of Announcement | 27/11/2024 |
| Product | Microsoft Exchange Server |
| CVE ID | CVE-2024-49040 |
| CVSS Score | 7.5 |
| Exploited in Wild | No |
| Patch/Remediation Available | Yes |
| Advisory Version | 1.0 |
Overview
On November 27, 2024, Microsoft re-released the November 2024 Security Updates (SUs) for Exchange Server to resolve an issue introduced in the initial release on November 12, 2024. The original update (SUv1) caused Exchange Server transport rules to intermittently stop functioning, particularly in environments using transport or Data Loss Protection (DLP) rules. The updated version (SUv2) addresses this issue.
Table of Actions for Admins:
| Scenario | Action Required |
| SUv1 installed manually, and transport/DLP rules are not used | Install SUv2 to regain control over the X-MS-Exchange-P2FromRegexMatch header. |
| SUv1 installed via Windows/Microsoft Update, no transport/DLP rules used | No immediate action needed; SUv2 will be installed automatically in December 2024. |
| SUv1 installed and then uninstalled due to transport rule issues | Install SUv2 immediately. |
| SUv1 never installed | Install SUv2 immediately. |
Remediation Steps
1. Immediate Actions
2. Monitor System Performance
3. Run SetupAssist Script for Issues
References:
New CheckPoint research discovered a new remote access trojan and information stealer used by Iranian state-sponsored actors to conduct reconnaissance of compromised endpoints and execute malicious commands.
Continue ReadingMaritime industry worldwide is witnessing massive changes in terms of continuous innovation and managing cyber risk on top priority list. In doing so enabling innovation becomes easier along with exploring various options that approaches and addresses cyber security in the maritime sector.
Now maritime professionals are ready to explore the latest industry trends and adopt solutions that dig deeper into maritime organizations’ challenges and priorities related to cyber security.
Intrucept Participates at the METS Trade 2024
Intrucept, a leader in cybersecurity solutions is excited to announce participation at the prestigious METS Trade 2024 in Amsterdam, Date Nov 19-21(2024).
This marks a significant step forward in transforming the maritime industry by combining the power of cutting-edge cybersecurity solutions.
About Intrucept: Ensuring Maritime Security in a Digital Age
As digital threats evolve, Intrucept is at the forefront of cyber security, providing comprehensive protection for maritime operations. From vessel systems to operational networks, we ensure that your fleet stays secure, resilient, and ready for the challenges of tomorrow.
Our solutions are designed to protect against cyberattacks, safeguard sensitive data, and maintain the integrity of vessel operations, all while enhancing overall business efficiency.
Why We’re Joining Forces at METS Trade 2024
At METS Trade 2024, we’ll be showcasing our unique partnership and how combining advanced cybersecurity with innovative engineering can provide unparalleled protection and efficiency for the maritime industry. Together, we are shaping the future of shipping — where digital security and operational excellence go hand in hand.
What You Can Expect from Our Joint Presence at METS 2024
Innovative cybersecurity solutions for shipping operations: Protect your vessels, data, and systems from the growing cyber threat landscape.
State-of-the-art shipping engineering technologies: Learn how we can optimize vessel performance, enhance fuel efficiency, and ensure compliance with global maritime standards.
Collaborative insights: Our team will be on hand to discuss how we can work together to make your operations safer, smarter, and more sustainable.
We invite you to visit our booth at METS Trade 2024 to explore how our solutions can help future-proof your business, improve operational resilience, and safeguard your digital infrastructure.
Details:
Event: METS Trade 2024
Dates: November 19-21, 2024
Location: Amsterdam RAI, Amsterdam, Netherlands
We look forward to meeting you and discussing how we can drive innovation, security, and efficiency in your maritime operations.