Privilege Escalation Vulnerability in ComboBlocks Plugin Affects Thousands of Sites
A critical vulnerability in the ComboBlocks WordPress plugin (formerly Post Grid and Gutenberg Blocks) exposes over 40,000 websites to potential complete takeover by unauthenticated attackers. This vulnerability exists due to improper handling of user meta during the registration process, enabling privilege escalation. It affects versions 2.2.85 to 2.3.3 and has been addressed in version 2.3.4.
OEM | WordPress |
Severity | Critical |
Date of Announcement | 2025-01-17 |
CVSS score | 9.8 |
CVE | CVE-2024-9636 |
Exploited in Wild | No |
Patch/Remediation Available | Yes |
Advisory Version | 1.0 |
Overview
ComboBlocks, a plugin designed to enhance website design and functionality, was found to have a critical security flaw (CVE-2024-9636) that could allow unauthenticated attackers to register as administrators, granting them full control over the affected websites.
Vulnerability Name | CVE ID | Product Affected | Severity | CVSS Score |
Unauthenticated Privilege Escalation | CVE-2024-9636 | ComboBlocks WordPress Plugin | Critical | 9.8 |
Technical Summary
CVE ID | System Affected | Vulnerability Details | Impact |
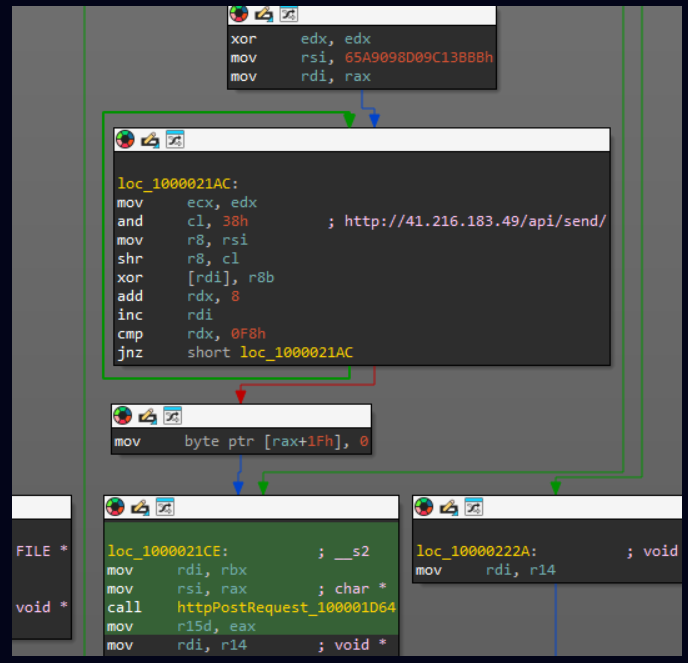
CVE-2024-9636 | ComboBlocks plugin (2.2.85 - 2.3.3) | The vulnerability stems from improper restriction of user meta updates during profile registration. This flaw allows unauthenticated attackers to register as administrators, granting them full control over the website. | Complete website takeover and malware injection. |
Remediations
- Update Plugin: Immediately update the ComboBlocks plugin to version 2.3.4 or later.
- Review Administrative Accounts:
- Audit all user accounts with administrative privileges.
- Revoke any unauthorized access.
- Enhance Security Posture:
- Enable multi-factor authentication (MFA) for all admin accounts.
- Restrict user permissions based on the principle of least privilege.
- Use a web application firewall (WAF) to filter and block malicious traffic.
- Monitor and Log Activity:
- Activate detailed logging for user registration and privilege changes.
- Configure alerts for unusual activity, such as mass registrations or privilege escalations.
- Implement Preventative Measures:
- Regularly update all plugins and themes.
- Backup the WordPress site frequently to ensure quick recovery in case of any compromise.