Threat Campaign Targeting WordPress Sites with Malicious Plugins
A rapidly escalating cyber threat targeting WordPress sites with malicious plugins. Malicious actors are breaching WordPress websites to install rogue plugins, which display fake software updates and error messages. These are being used to distribute information-stealing malware.
Threat Overview
Since 2023, a malicious campaign known as ClearFake has been exploiting compromised websites to display fake browser update banners that trick users into downloading malware. This campaign evolved in 2024 with the introduction of ClickFix, a more advanced variant. ClickFix campaigns are more sophisticated and use fake error messages for browsers, web conferences, social media platforms, and even captcha pages to mislead users. The supposed “fixes” are actually PowerShell scripts designed to install malware capable of stealing sensitive information, such as login credentials.
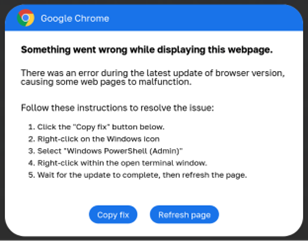
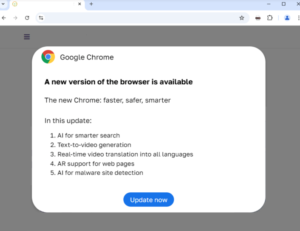
An example ClickFix overlay pretending to be a Chrome error Fake Google update banner
Source: BleepingComputer Source: Randy McEoin
Recent Findings
Bleepingcomputer reported that over 6,000 WordPress sites have been compromised as part of this campaign. The attackers are installing malicious plugins that closely resemble legitimate ones, such as “Wordfence Security” or “LiteSpeed Cache,” to evade detection. These plugins secretly inject malicious JavaScript into the HTML of affected websites, leading to the display of fraudulent updates or error messages.
Here is the list of malicious plugins identified from June to September 2024:
LiteSpeed Cache Classic | Custom CSS Injector |
MonsterInsights Classic | Custom Footer Generator |
Wordfence Security Classic | Custom Login Styler |
Search Rank Enhancer | Dynamic Sidebar Manager |
SEO Booster Pro | Easy Themes Manager |
Google SEO Enhancer | Form Builder Pro |
Rank Booster Pro | Quick Cache Cleaner |
Admin Bar Customizer | Responsive Menu Builder |
Advanced User Manager | SEO Optimizer Pro |
Advanced Widget Manage | Simple Post Enhancer |
Content Blocker | Social Media Integrator |
The threat actors appear to be utilizing stolen admin credentials to directly log into WordPress sites. These credentials are likely obtained through a combination of brute force attacks, phishing, or pre-existing malware infections. Once they gain access, the attackers are able to install these plugins without the need to visit the login page, streamlining the attack process.
Recommendations
If you are using a WordPress site, we recommend the following immediate actions:
- Ensure all the plugins installed are trusted, if anything suspicious remove them immediately.
- Keep your passwords to strong, unique ones that are not used anywhere else.
- Enable 2FA for all administrative users to protect against unauthorized access.
- Regularly review your access logs for any unusual login attempts or plugin installations etc.
Always stay vigilant and take proactive measures to protect your digital assets.
Recent Posts
- Critical Credential Reuse Vulnerability in Cisco ISE Cloud Deployments
- Reflected XSS Vulnerability in Splunk Enterprise & Cloud Platform
- High Risk DoS Vulnerability in ModSecurity WAF
- Critical Vulnerabilities Patched in IBM QRadar Suite & Cloud Pak for Security
- Critical 0-Day Vulnerabilities in Qualcomm Adreno GPU Drivers Actively Exploited
Recent Comments
Search
Recent Comments
Recent Posts
- Critical Credential Reuse Vulnerability in Cisco ISE Cloud Deployments 6 June 2025
- Reflected XSS Vulnerability in Splunk Enterprise & Cloud Platform 5 June 2025
- High Risk DoS Vulnerability in ModSecurity WAF 4 June 2025
- Critical Vulnerabilities Patched in IBM QRadar Suite & Cloud Pak for Security 4 June 2025
Archives
- June 2025 (7)
- May 2025 (19)
- April 2025 (18)
- March 2025 (21)
- February 2025 (18)
- January 2025 (22)
- December 2024 (10)
- November 2024 (8)
- October 2024 (6)
- September 2024 (3)
- October 2023 (9)
- June 2023 (4)
