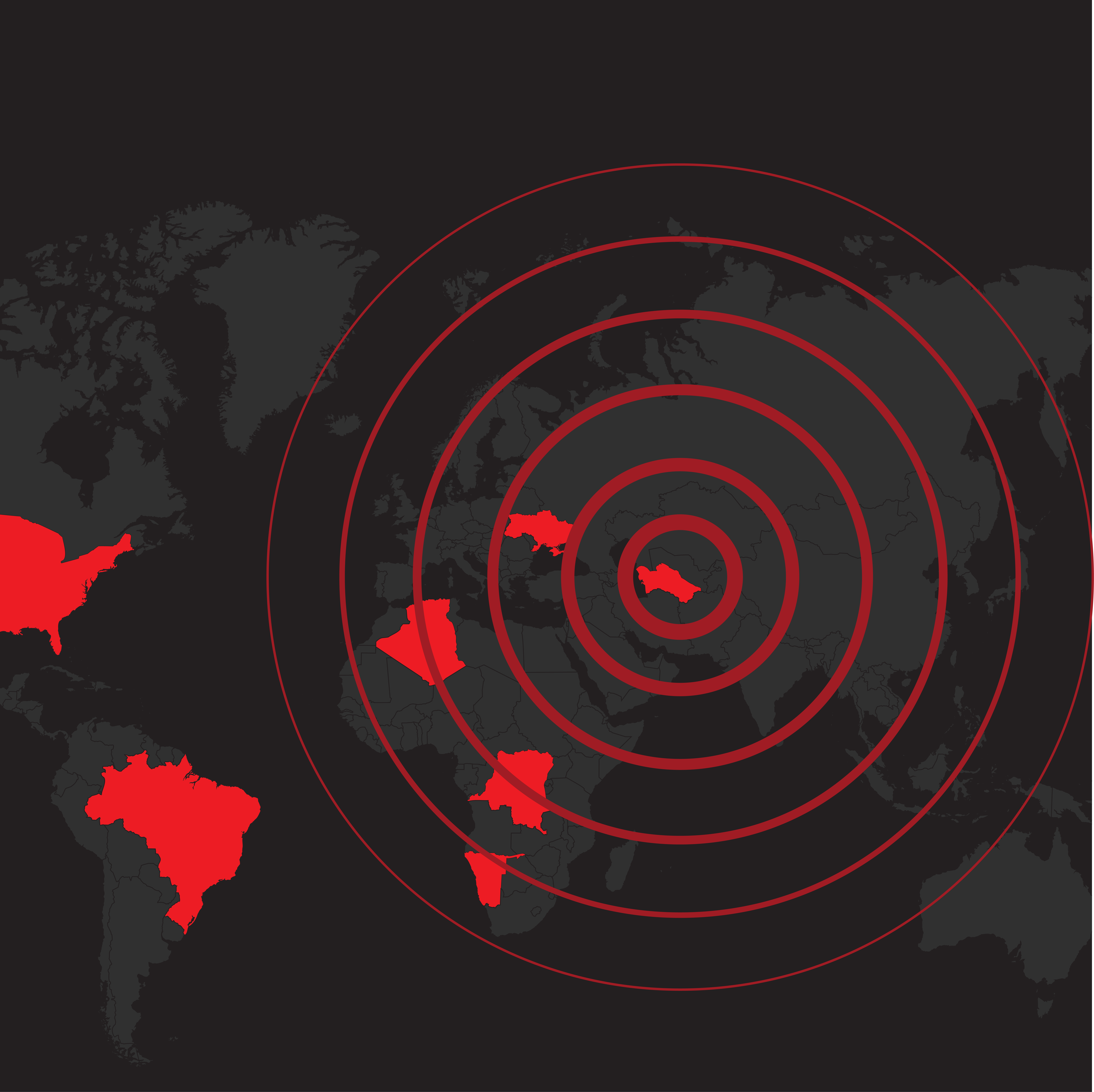
Detect threats anywhere
Intru360 gives security analysts and SOC managers a clear view across the organization, helping them fully understand the extent and context of an attack. It also simplifies workflows by automatically handling alerts, allowing for faster detection of both known and unknown threats.
Identify latest threats without having to purchase, implement, and oversee several solutions or find, hire, and manage a team security analyst.
Unify latest threat intelligence and security technologies to prioritize the threats that pose the greatest risk to your company.
Here are some features we offer:
- Over 400 third-party and cloud integrations.
- More than 1,100 preconfigured correlation rules.
- Ready-to-use threat analytics, threat intelligence service feeds, and prioritization based on risk.
- Prebuilt playbooks and automated response capabilities.

Solution Highlights

Log Management (SIEM)
Enterprise Log Management and Correlation
- Our next gen SIEM is a comprehensive solution for Security Information and Event Management. It gathers, interprets, and centralizes all security data for organizations.
- Unlike many SIEM systems, our solution retains all events and log data, not just alert-related information.
- This is crucial given varying data retention needs based on compliance and organizational policies.
- Our solution ensures log retention for up to 5 years, catering to diverse requirements.

Easy log exploration.
Build custom dashboards easily.

SOC, ISO, HIPAA, GDPR, etc.

Unify logs, detect threats.

Automated solutions for threats.

Alert on bad configurations.
Compliance Management
Ensure Compliance and Minimize Your Attack Surface
- Speed up and streamline compliance management for all common standards (ISO, SOC2, GDPR, HIPAA, etc.) with our integrated tools and services.
- Our solution is more thorough, cost-effective, and quicker to deliver results.
- Access all the necessary functionalities to assess compliance across various standards, all within one platform.
- Uncover IP-enabled assets with OS specifics.
- Spot vulnerabilities, patch gaps, and fix insecure setups.
- Automatically correlate security events using 1000+ predefined rules.
- Detect lurking threats like botnets and trojans.
- Analyze threat objectives for network protection.
- Respond swiftly with remediation advice and incident oversight.
- Monitor and report to ensure compliance.

Vulnerability Management
Manage Vulnerabilities and Keep Your Devices Risk Free
- Proactively identify and remediate vulnerabilities across your IT infrastructure.
- Conduct regular vulnerability scans, prioritize risks, and implement corrective measures to fortify defenses and reduce security gaps.
- Identify misconfigurations, assess compliance with best practices, and optimize cloud security controls for enhanced resilience
RESPOND
Swift Action for Security Incidents
- Conduct comprehensive forensic investigations with powerful querying capabilities.
- Uncover root causes, trace attack paths, and gather critical evidence for incident response and threat remediation.
- Streamline incident response workflows with automation and orchestration.
- Stay informed and organized with real-time notifications and integrated ticketing systems.


Dark Web Monitoring
Uncover, Analyse, Act
- Proactively identify and remediate vulnerabilities across your IT infrastructure.
- Conduct regular vulnerability scans, prioritize risks, and implement corrective measures to fortify defenses and reduce security gaps.
- Identify misconfigurations, assess compliance with best practices, and optimize cloud security controls for enhanced resilience.
- Monitor the dark web for potential threats and data breaches affecting your organization.
- Simplify compliance management with pre-built reporting templates. Generate audit-ready reports for regulatory requirements.
- Gain actionable insights from pre-built event reporting templates.
- Create personalized visualizations, monitor key metrics, and gain real-time visibility into security posture, enabling quick decision-making and effective risk management.
- Retain historical data, perform log correlation, and ensure data integrity to support forensic investigations and regulatory requirements.
REPORT
Data-Driven Security Insights
Why Choose SecureOps?
Empower Your Security Operations
Ease Of Visibility
Ease Of Alert to Real Time Threats
Ease Of Compliance
Ease Of Data & Logs
Get Ahead of Threats
Don’t wait for threats to become breaches. Stay proactive with SecureOps and take your Cyber defense strategy to the next level.
Key Features
Know who and what is connected to your environment at all times.
Know where the vulnerabilities are on your assets to avoid compromise.

Know when suspicious activities happen in your environment.
Continuously monitor your endpoints in the cloud and on premises to detect threats and changes to critical files.

Identify suspicious behavior and potentially compromised systems.

Correlate and analyze security event data from across your network and respond.

Pre-built, customizable reports for regulation standards and compliance frameworks.

Broad set of data collection methods to automatically collect security-relevant data.



